Today I played around with tcpdump/wireshark/curl to analyze/replay some HTTP traffic sent by my browser to usps - in particular I was analyzing the form data that was submitted in their 'tracking confirmation' service.
I first set tcpdump on the desktop to capture traffic going to port 80, and then hit the 'submit' button on the tracking service page on usps. After I got the data from the service, I quit from tcpdump (Ctrl+C) and then looked at the generated raw dump (file) with wireshark.
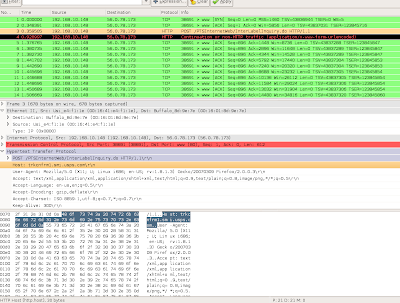
Wireshark showed me the post data used in the form, and I used curl to replay the data back to the usps web server, and it returned me the html including my delivery confirmation data.
Since the tracking codes seem rather sequential, one can imagine an attack where a script runs many requests against the usps server and obtains a mega list of information about package delivery.
Here are the steps:
1. run tcpdump on the desktop:
tcpdump -a -x -i eth0 tcp dst port 80 -s 1024 -w /home/user/tcp.dump
2. enter the tracking number and hit 'Go' button at http://trkcnfrm1.smi.usps.com
3. after the browser has retrieved the data, quit tcpdump (Ctrl+C) on the command line
4. analyze the raw file (/home/user/tcp.dump) using wireshark
5. look for the HTTP packets, on one you will see the post data that looks like this:
origTrackNum=0307+0020+0000+8347+7000&Go+to+Track+and+Confirm+Label+%2F+Receipt+Number+Page.x=19&Go+to+Track+and+Confirm+Label+%2F+Receipt+Number+Page.y=7&Go+to+Track+and+Confirm+Label+%2F+Receipt+Number+Page=Go
6. to replay the data, run curl with this data as post data against the host found in the HTTP header (in wireshark) as follows (don't forget to enclose the post data within quotes):
curl -d 'origTrackNum=0307+0020+0000+8347+7000&Go+to+Track+and+Confirm+Label+%2F+Receipt+Number+Page.x=19&Go+to+Track+and+Confirm+Label+%2F+Receipt+Number+Page.y=7&Go+to+Track+and+Confirm+Label+%2F+Receipt+Number+Page=Go' http://trkcnfrm1.smi.usps.com/PTSInternetWeb/InterLabelInquiry.do
7. observe the html that the server returns (which has the delivery confirmation details)
No comments:
Post a Comment